|
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
由於快速區塊鏈技術開發,銀行,醫療保健,保險和物聯網已採用了智能合約(SC)
Smart contracts (SCs) are adopted by banking, healthcare, insurance, and the Internet of Things (IoT) due to rapid blockchain technology development1. They pose security risks because of their programming and operating environment. The BeautyChain (BEC) Token Attack and Proof of Weak Hand (PoWH) event focuses on shrinking smart contract (SC) vulnerabilities.
智能合約(SC)通過快速區塊鏈技術開發而採用銀行,醫療保健,保險和物聯網(IoT)1。由於其編程和操作環境,它們構成了安全風險。美容鏈(BEC)令牌攻擊和弱手(POWH)事件的證明著重於縮小智能合約(SC)脆弱性。
Attackers exploited BEC, an Ethereum-based token, due to a SC vulnerability. PoWH, another SC-related Ponzi scheme, had similar weaknesses. The BEC cryptocurrency SC had an integer overflow in April 2018, allowing hackers to crash the market by issuing excessive tokens. The PoWH contract lost Ether due to similar issues2,3. These incidents highlight the importance of integer overflow detection, included in our detection method.
由於SC脆弱性,攻擊者利用了以太坊的代幣BEC。 Powh是另一種與SC相關的龐氏騙局,具有相似的弱點。 BEC加密貨幣SC在2018年4月的整數溢出中溢出,使黑客能夠通過發行過多的令牌來崩潰市場。由於類似的發行,POWH合同損失了以太2,3。這些事件突出了我們檢測方法中包括的整數溢出檢測的重要性。
We propose an accurate and adaptive technique to detect the integer overflow vulnerability in Ethereum-based SCs. A difficulty in making a model to detect vulnerabilities is collecting the source code of SCs to test them. Related research shows that about one percent of the SC source code is visible to the public4. The Ethereum network and node constraints make collecting sufficient and useful source codes labor- and resource-intensive.
我們提出了一種準確的自適應技術,以檢測基於以太坊的SC中的整數溢出脆弱性。製作模型檢測漏洞的困難是收集SC的源代碼來測試它們。相關研究表明,公共4可以看到SC源代碼的百分之一。以太坊網絡和節點約束使收集足夠且有用的源代碼勞動力和資源密集型。
A crucial step is performing a comprehensive quality and security check of the collected dataset. There are privacy and legal issues in collecting real vulnerability data5. It’s vital to pay attention to the quantity and quality of the collected data when building a trustworthy machine-learning model for code representation and vulnerability identification. Good samples are needed to build accurate and generalizable models. A lack of data can affect the model’s ability to identify vulnerabilities.
關鍵步驟是對收集的數據集進行全面的質量和安全檢查。收集真正的漏洞數據有隱私和法律問題5。在建立可信賴的機器學習模型以用於代碼表示和漏洞識別時,請注意收集數據的數量和質量。需要好的樣本來構建準確且可推廣的模型。缺乏數據會影響模型識別漏洞的能力。
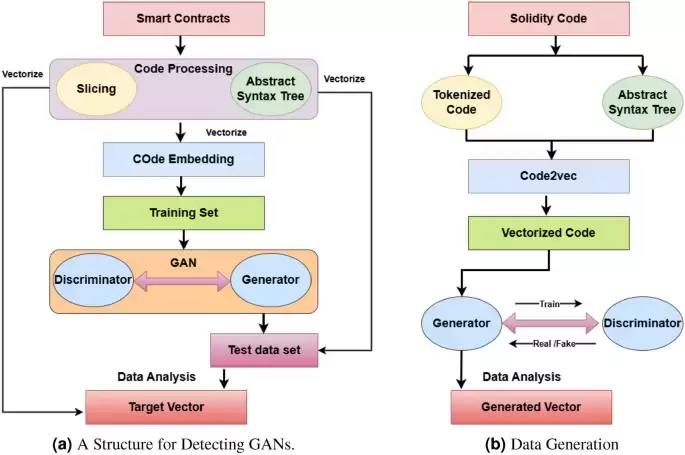
To overcome these challenges, we propose a few-shot learning approach for detecting SC vulnerabilities using data augmentation techniques derived from traditional machine learning. We introduce Generative Adversarial Networks (GAN) technology for efficient vulnerability detection. GANs comprise generators and discriminators6. The generator generates data, and the discriminator compares the generated data with real data.
為了克服這些挑戰,我們提出了一種使用來自傳統機器學習的數據增強技術來檢測SC漏洞的幾種學習方法。我們引入生成對抗網絡(GAN)技術,以進行有效的脆弱性檢測。 GAN包括發電機和歧視器6。發電機生成數據,鑑別器將生成的數據與真實數據進行比較。
Crucially for data augmentation, we employ GAN generators to continually construct synthetic contracts that closely resemble real SCs. We have trained the discriminator to distinguish between genuine and fabricated contracts. This aspect helps to resolve the issue of insufficient data7. We maintain semantic and syntactic integrity by converting SC source code into spatial vectors using a code embedding technique8. GAN can handle small samples by training a vector data set with a small set of samples to generate several fake data sets that can be used to compare similarities.
對於數據增強至關重要的是,我們使用GAN發電機來不斷構建與實際SC相似的合成合同。我們已經培訓了歧視者,以區分真正的合同和捏造合同。這方面有助於解決數據不足的問題7。我們通過使用代碼嵌入技術將SC源代碼轉換為空間向量8來維護語義和句法完整性8。 GAN可以通過訓練一個少量樣品來處理矢量數據集來處理小樣本,以生成幾個可用於比較相似性的虛假數據集。
Our approach combines vector similarity analysis with feedback from the GAN discriminator to detect SC integer overflow vulnerabilities. The model incorporates GAN’s adversarial training approach and generates essential characteristics from SCs to make SC security analysis more accurate and efficient9.
我們的方法將矢量相似性分析與GAN INCINETATER的反饋相結合,以檢測SC整數溢出漏洞。該模型結合了GAN的對抗訓練方法,並從SCS產生了基本特徵,以使SC安全分析更加準確,有效9。
This work was supported in part by the National Natural Science Foundation of China (No. 62208048), the Beijing Natural Science Foundation (No. 4223035), and the Key Research and Development Program of China (No. 2023YHA52001).
這項工作得到了中國國家自然科學基金會(第62208048號),北京自然科學基金會(第4223035號)和中國的主要研發計劃(第2023YHA52001號)的部分支持。
This article can be accessed via the following link: https://arxiv.org/abs/2308.01141
可以通過以下鏈接訪問本文:https://arxiv.org/abs/2308.01141
Smart contract (SC) vulnerability detection is critical to ensure security and trustworthiness10. Traditional methods, including fuzzing, symbolic execution, and formal verification, have limitations in terms of automation, efficiency, and accuracy. Recent efforts have focused on analyzing SC source code, but issues remain in preserving code structure, managing diverse information, and reducing dependence on large datasets11. Furthermore, current feature-learning approaches struggle with effectively predicting vulnerabilities12. Addressing these shortcomings is crucial to improving SC security.
智能合約(SC)漏洞檢測對於確保安全性和可信度10至關重要。傳統方法,包括模糊,象徵性執行和正式驗證,在自動化,效率和準確性方面存在局限性。最近的努力集中在分析SC源代碼上,但是在保存代碼結構,管理多樣的信息以及減少對大型數據集的依賴11中仍然存在問題。 1111。此外,當前的特徵學習方法與有效預測脆弱性的方法很難12。解決這些缺點對於提高SC安全性至關重要。
Recently, blockchain technology, especially smart contracts (SCs), have been rapidly adopted by banking, healthcare, insurance, and the Internet of Things (IoT)1. However, SCs pose significant security risks due to their programming and operating environment. A recent case of the BeautyChain (BEC) Token Attack and Proof of Weak Hand (PoWH) event focuses on shrinking smart contract (SC) vulnerabilities.
最近,銀行,醫療保健,保險和物聯網(IoT)1迅速採用了區塊鏈技術,尤其是智能合約(SCS)。但是,由於其編程和操作環境,SCS構成了嚴重的安全風險。最新的美容鏈(BEC)代幣攻擊和虛弱(POWH)事件證明的案例側重於減少智能合約(SC)脆弱性。
As reported by blockchain media, attackers exploited BEC, an Ethereum-based token, due to a SC vulnerability. PoWH, another SC-related Ponzi scheme, had similar weaknesses. The BEC cryptocurrency SC had an integer overflow in April 2018, allowing hackers to completely crash the market by issuing an nearly unlimited supply of tokens. The PoWH contract on the Ethereum blockchain lost nearly 3000 Ether due to similar issues2,3. These incidents highlight the importance of integer overflow detection, which is included in our detection method.
正如區塊鏈媒體報導的那樣,由於SC脆弱性,攻擊者利用了基於以太坊的代幣BEC。 Powh是另一種與SC相關的龐氏騙局,具有相似的弱點。 BEC加密貨幣SC在2018年4月的整數溢出中溢出,使黑客能夠通過發出幾乎無限的代幣供應來完全崩潰市場。由於類似的發行,以太坊區塊鏈上的POWH合同損失了近3000個以太。這些事件強調了整數溢出檢測的重要性,這包括我們的檢測方法中。
We propose an accurate and adaptive technique to detect the integer overflow vulnerability in Ethereum-based SCs. A difficulty in making a model to detect vulnerabilities is collecting the source code of SCs to test them. According to related research, only about one percent of the source code for SCs can be seen by the public4. Due to the constraints of the Ethereum network and nodes, collecting sufficient and useful source codes is
我們提出了一種準確的自適應技術,以檢測基於以太坊的SC中的整數溢出脆弱性。製作模型檢測漏洞的困難是收集SC的源代碼來測試它們。根據相關研究,public4只能看到SC的源代碼的大約百分之一。由於以太坊網絡和節點的限制,收集足夠有用的源代碼是
免責聲明:info@kdj.com
所提供的資訊並非交易建議。 kDJ.com對任何基於本文提供的資訊進行的投資不承擔任何責任。加密貨幣波動性較大,建議您充分研究後謹慎投資!
如果您認為本網站使用的內容侵犯了您的版權,請立即聯絡我們(info@kdj.com),我們將及時刪除。
-

-

- PI網絡:導航KYC延遲和尋求獎勵
- 2025-07-12 20:50:12
- 探索PI網絡的KYC延遲,獎勵分銷策略以及社區對權力下放的看法。
-

- 比特幣,加密和比爾:紐約人付款指南!
- 2025-07-12 20:30:12
- 厭倦了同樣的舊賬單日常工作?探索使用比特幣和加密貨幣來償還債務,但請仔細踩踏!波動和費用正在等待。
-

-

-

-

-

-