|
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
由于快速区块链技术开发,银行,医疗保健,保险和物联网已采用了智能合约(SC)
Smart contracts (SCs) are adopted by banking, healthcare, insurance, and the Internet of Things (IoT) due to rapid blockchain technology development1. They pose security risks because of their programming and operating environment. The BeautyChain (BEC) Token Attack and Proof of Weak Hand (PoWH) event focuses on shrinking smart contract (SC) vulnerabilities.
智能合约(SC)通过快速区块链技术开发而采用银行,医疗保健,保险和物联网(IoT)1。由于其编程和操作环境,它们构成了安全风险。美容链(BEC)令牌攻击和弱手(POWH)事件的证明着重于缩小智能合约(SC)脆弱性。
Attackers exploited BEC, an Ethereum-based token, due to a SC vulnerability. PoWH, another SC-related Ponzi scheme, had similar weaknesses. The BEC cryptocurrency SC had an integer overflow in April 2018, allowing hackers to crash the market by issuing excessive tokens. The PoWH contract lost Ether due to similar issues2,3. These incidents highlight the importance of integer overflow detection, included in our detection method.
由于SC脆弱性,攻击者利用了以太坊的代币BEC。 Powh是另一种与SC相关的庞氏骗局,具有相似的弱点。 BEC加密货币SC在2018年4月的整数溢出中溢出,使黑客能够通过发行过多的令牌来崩溃市场。由于类似的发行,POWH合同损失了以太2,3。这些事件突出了我们检测方法中包括的整数溢出检测的重要性。
We propose an accurate and adaptive technique to detect the integer overflow vulnerability in Ethereum-based SCs. A difficulty in making a model to detect vulnerabilities is collecting the source code of SCs to test them. Related research shows that about one percent of the SC source code is visible to the public4. The Ethereum network and node constraints make collecting sufficient and useful source codes labor- and resource-intensive.
我们提出了一种准确的自适应技术,以检测基于以太坊的SC中的整数溢出脆弱性。制作模型检测漏洞的困难是收集SC的源代码来测试它们。相关研究表明,公共4可以看到SC源代码的百分之一。以太坊网络和节点约束使收集足够且有用的源代码劳动力和资源密集型。
A crucial step is performing a comprehensive quality and security check of the collected dataset. There are privacy and legal issues in collecting real vulnerability data5. It’s vital to pay attention to the quantity and quality of the collected data when building a trustworthy machine-learning model for code representation and vulnerability identification. Good samples are needed to build accurate and generalizable models. A lack of data can affect the model’s ability to identify vulnerabilities.
关键步骤是对收集的数据集进行全面的质量和安全检查。收集真正的漏洞数据有隐私和法律问题5。在建立可信赖的机器学习模型以用于代码表示和漏洞识别时,请注意收集数据的数量和质量。需要好的样本来构建准确且可推广的模型。缺乏数据会影响模型识别漏洞的能力。
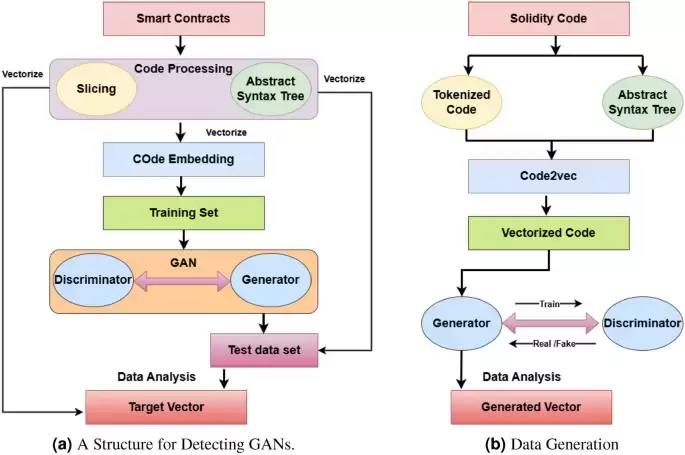
To overcome these challenges, we propose a few-shot learning approach for detecting SC vulnerabilities using data augmentation techniques derived from traditional machine learning. We introduce Generative Adversarial Networks (GAN) technology for efficient vulnerability detection. GANs comprise generators and discriminators6. The generator generates data, and the discriminator compares the generated data with real data.
为了克服这些挑战,我们提出了一种使用来自传统机器学习的数据增强技术来检测SC漏洞的几种学习方法。我们引入生成对抗网络(GAN)技术,以进行有效的脆弱性检测。 GAN包括发电机和歧视器6。发电机生成数据,鉴别器将生成的数据与真实数据进行比较。
Crucially for data augmentation, we employ GAN generators to continually construct synthetic contracts that closely resemble real SCs. We have trained the discriminator to distinguish between genuine and fabricated contracts. This aspect helps to resolve the issue of insufficient data7. We maintain semantic and syntactic integrity by converting SC source code into spatial vectors using a code embedding technique8. GAN can handle small samples by training a vector data set with a small set of samples to generate several fake data sets that can be used to compare similarities.
对于数据增强至关重要的是,我们使用GAN发电机来不断构建与实际SC相似的合成合同。我们已经培训了歧视者,以区分真正的合同和捏造合同。这方面有助于解决数据不足的问题7。我们通过使用代码嵌入技术将SC源代码转换为空间向量8来维护语义和句法完整性8。 GAN可以通过训练一个少量样品来处理矢量数据集来处理小样本,以生成几个可用于比较相似性的虚假数据集。
Our approach combines vector similarity analysis with feedback from the GAN discriminator to detect SC integer overflow vulnerabilities. The model incorporates GAN’s adversarial training approach and generates essential characteristics from SCs to make SC security analysis more accurate and efficient9.
我们的方法将矢量相似性分析与GAN INCINETATER的反馈相结合,以检测SC整数溢出漏洞。该模型结合了GAN的对抗训练方法,并从SCS产生了基本特征,以使SC安全分析更加准确,有效9。
This work was supported in part by the National Natural Science Foundation of China (No. 62208048), the Beijing Natural Science Foundation (No. 4223035), and the Key Research and Development Program of China (No. 2023YHA52001).
这项工作得到了中国国家自然科学基金会(第62208048号),北京自然科学基金会(第4223035号)和中国的主要研发计划(第2023YHA52001号)的部分支持。
This article can be accessed via the following link: https://arxiv.org/abs/2308.01141
可以通过以下链接访问本文:https://arxiv.org/abs/2308.01141
Smart contract (SC) vulnerability detection is critical to ensure security and trustworthiness10. Traditional methods, including fuzzing, symbolic execution, and formal verification, have limitations in terms of automation, efficiency, and accuracy. Recent efforts have focused on analyzing SC source code, but issues remain in preserving code structure, managing diverse information, and reducing dependence on large datasets11. Furthermore, current feature-learning approaches struggle with effectively predicting vulnerabilities12. Addressing these shortcomings is crucial to improving SC security.
智能合约(SC)漏洞检测对于确保安全性和可信度10至关重要。传统方法,包括模糊,象征性执行和正式验证,在自动化,效率和准确性方面存在局限性。最近的努力集中在分析SC源代码上,但是在保存代码结构,管理多样的信息以及减少对大型数据集的依赖11中仍然存在问题。1111。此外,当前的特征学习方法与有效预测脆弱性的方法很难12。解决这些缺点对于提高SC安全性至关重要。
Recently, blockchain technology, especially smart contracts (SCs), have been rapidly adopted by banking, healthcare, insurance, and the Internet of Things (IoT)1. However, SCs pose significant security risks due to their programming and operating environment. A recent case of the BeautyChain (BEC) Token Attack and Proof of Weak Hand (PoWH) event focuses on shrinking smart contract (SC) vulnerabilities.
最近,银行,医疗保健,保险和物联网(IoT)1迅速采用了区块链技术,尤其是智能合约(SCS)。但是,由于其编程和操作环境,SCS构成了严重的安全风险。最新的美容链(BEC)代币攻击和虚弱(POWH)事件证明的案例侧重于减少智能合约(SC)脆弱性。
As reported by blockchain media, attackers exploited BEC, an Ethereum-based token, due to a SC vulnerability. PoWH, another SC-related Ponzi scheme, had similar weaknesses. The BEC cryptocurrency SC had an integer overflow in April 2018, allowing hackers to completely crash the market by issuing an nearly unlimited supply of tokens. The PoWH contract on the Ethereum blockchain lost nearly 3000 Ether due to similar issues2,3. These incidents highlight the importance of integer overflow detection, which is included in our detection method.
正如区块链媒体报道的那样,由于SC脆弱性,攻击者利用了基于以太坊的代币BEC。 Powh是另一种与SC相关的庞氏骗局,具有相似的弱点。 BEC加密货币SC在2018年4月的整数溢出中溢出,使黑客能够通过发出几乎无限的代币供应来完全崩溃市场。由于类似的发行,以太坊区块链上的POWH合同损失了近3000个以太。这些事件强调了整数溢出检测的重要性,这包括我们的检测方法中。
We propose an accurate and adaptive technique to detect the integer overflow vulnerability in Ethereum-based SCs. A difficulty in making a model to detect vulnerabilities is collecting the source code of SCs to test them. According to related research, only about one percent of the source code for SCs can be seen by the public4. Due to the constraints of the Ethereum network and nodes, collecting sufficient and useful source codes is
我们提出了一种准确的自适应技术,以检测基于以太坊的SC中的整数溢出脆弱性。制作模型检测漏洞的困难是收集SC的源代码来测试它们。根据相关研究,public4只能看到SC的源代码的大约百分之一。由于以太坊网络和节点的限制,收集足够有用的源代码是
免责声明:info@kdj.com
所提供的信息并非交易建议。根据本文提供的信息进行的任何投资,kdj.com不承担任何责任。加密货币具有高波动性,强烈建议您深入研究后,谨慎投资!
如您认为本网站上使用的内容侵犯了您的版权,请立即联系我们(info@kdj.com),我们将及时删除。
-

- 埃迪(Eddie)摇滚皇家造币厂:铁娘的50周年获得硬币化!
- 2025-07-12 16:30:11
- Iron Maiden成立50周年的纪念硬币以Eddie为特色,巩固了他们的传奇地位。年龄的金属致敬!
-

-

- XLM Price在出色的升级嗡嗡声中飙升:$ 1可触及?
- 2025-07-12 17:10:12
- XLM正在引起浪潮,这是对协议23和看涨技术指标的预期驱动的。恒星可以维持势头并达到新的高度吗?
-

-

-

- 恒星的价格上涨:Defi增长及其对您意味着什么
- 2025-07-12 18:10:12
- Stellar(XLM)正在上升!在网络升级和DEFI增长的推动下,XLM显示了新高点的潜力。发现推动这一激增的关键因素。
-

-

- XLM价格,Defi扩展和网络升级:出色的未来?
- 2025-07-12 18:10:12
- Stellar(XLM)正在使用协议23,DEFI扩展和网络升级获得动力。这些催化剂会将XLM推向新的高度吗?
-