|
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
Cryptocurrency News Articles
Generative Adversarial Networks for Detecting Integer Overflow Vulnerabilities in Smart Contracts
May 03, 2025 at 09:55 pm
Smart contracts (SCs) have been adopted by banking, healthcare, insurance, and the IoT because of rapid blockchain technology development1
Smart contracts (SCs) are adopted by banking, healthcare, insurance, and the Internet of Things (IoT) due to rapid blockchain technology development1. They pose security risks because of their programming and operating environment. The BeautyChain (BEC) Token Attack and Proof of Weak Hand (PoWH) event focuses on shrinking smart contract (SC) vulnerabilities.
Attackers exploited BEC, an Ethereum-based token, due to a SC vulnerability. PoWH, another SC-related Ponzi scheme, had similar weaknesses. The BEC cryptocurrency SC had an integer overflow in April 2018, allowing hackers to crash the market by issuing excessive tokens. The PoWH contract lost Ether due to similar issues2,3. These incidents highlight the importance of integer overflow detection, included in our detection method.
We propose an accurate and adaptive technique to detect the integer overflow vulnerability in Ethereum-based SCs. A difficulty in making a model to detect vulnerabilities is collecting the source code of SCs to test them. Related research shows that about one percent of the SC source code is visible to the public4. The Ethereum network and node constraints make collecting sufficient and useful source codes labor- and resource-intensive.
A crucial step is performing a comprehensive quality and security check of the collected dataset. There are privacy and legal issues in collecting real vulnerability data5. It’s vital to pay attention to the quantity and quality of the collected data when building a trustworthy machine-learning model for code representation and vulnerability identification. Good samples are needed to build accurate and generalizable models. A lack of data can affect the model’s ability to identify vulnerabilities.
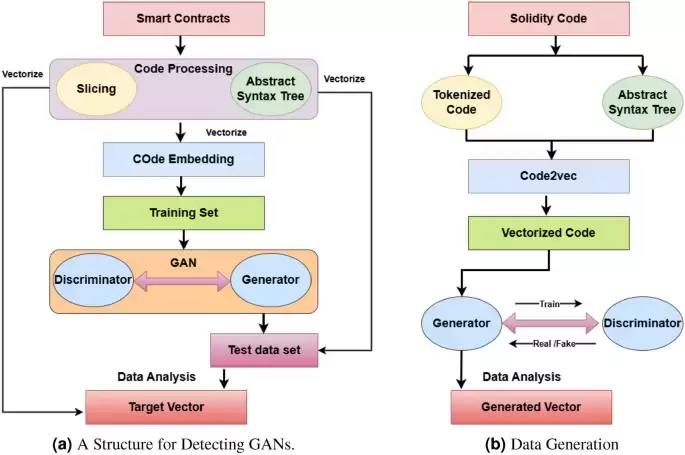
To overcome these challenges, we propose a few-shot learning approach for detecting SC vulnerabilities using data augmentation techniques derived from traditional machine learning. We introduce Generative Adversarial Networks (GAN) technology for efficient vulnerability detection. GANs comprise generators and discriminators6. The generator generates data, and the discriminator compares the generated data with real data.
Crucially for data augmentation, we employ GAN generators to continually construct synthetic contracts that closely resemble real SCs. We have trained the discriminator to distinguish between genuine and fabricated contracts. This aspect helps to resolve the issue of insufficient data7. We maintain semantic and syntactic integrity by converting SC source code into spatial vectors using a code embedding technique8. GAN can handle small samples by training a vector data set with a small set of samples to generate several fake data sets that can be used to compare similarities.
Our approach combines vector similarity analysis with feedback from the GAN discriminator to detect SC integer overflow vulnerabilities. The model incorporates GAN’s adversarial training approach and generates essential characteristics from SCs to make SC security analysis more accurate and efficient9.
This work was supported in part by the National Natural Science Foundation of China (No. 62208048), the Beijing Natural Science Foundation (No. 4223035), and the Key Research and Development Program of China (No. 2023YHA52001).
This article can be accessed via the following link: https://arxiv.org/abs/2308.01141
Smart contract (SC) vulnerability detection is critical to ensure security and trustworthiness10. Traditional methods, including fuzzing, symbolic execution, and formal verification, have limitations in terms of automation, efficiency, and accuracy. Recent efforts have focused on analyzing SC source code, but issues remain in preserving code structure, managing diverse information, and reducing dependence on large datasets11. Furthermore, current feature-learning approaches struggle with effectively predicting vulnerabilities12. Addressing these shortcomings is crucial to improving SC security.
Recently, blockchain technology, especially smart contracts (SCs), have been rapidly adopted by banking, healthcare, insurance, and the Internet of Things (IoT)1. However, SCs pose significant security risks due to their programming and operating environment. A recent case of the BeautyChain (BEC) Token Attack and Proof of Weak Hand (PoWH) event focuses on shrinking smart contract (SC) vulnerabilities.
As reported by blockchain media, attackers exploited BEC, an Ethereum-based token, due to a SC vulnerability. PoWH, another SC-related Ponzi scheme, had similar weaknesses. The BEC cryptocurrency SC had an integer overflow in April 2018, allowing hackers to completely crash the market by issuing an nearly unlimited supply of tokens. The PoWH contract on the Ethereum blockchain lost nearly 3000 Ether due to similar issues2,3. These incidents highlight the importance of integer overflow detection, which is included in our detection method.
We propose an accurate and adaptive technique to detect the integer overflow vulnerability in Ethereum-based SCs. A difficulty in making a model to detect vulnerabilities is collecting the source code of SCs to test them. According to related research, only about one percent of the source code for SCs can be seen by the public4. Due to the constraints of the Ethereum network and nodes, collecting sufficient and useful source codes is
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.