|
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
深入研究GMX的利用,其對流動性池的影響以及對Defi安全性的更廣泛含義。是運氣不好還是系統性問題?
GMX Exploit: $42M Liquidity Pool Hack Exposes DeFi Security Flaws
GMX利用:4200萬美元的流動性池黑客揭露Defi安全缺陷
Yo, crypto fam! It's been a wild week in DeFi, and not in a good way. The GMX exploit is making headlines, and it's a wake-up call for everyone involved in decentralized finance. Let's break down what happened, why it matters, and what we can learn from it.
喲,加密貨幣。在Defi中是一個狂野的一周,而且不是很好。 GMX漏洞利用是頭條新聞,這是對所有參與分散金融的人的警鐘。讓我們分解發生的事情,為什麼重要以及我們可以從中學到什麼。
What Went Down? The GMX V1 Exploit
發生了什麼? GMX V1利用
On July 9, 2025, GMX V1's GLP liquidity pool on Arbitrum got hit HARD. Hackers made off with a staggering $42 million. The team reacted swiftly, halting trading, minting, and redeeming for GLP on both Arbitrum and Avalanche. The damage was contained to GMX V1; GMX V2 and the GMX token are reportedly safe. But still...ouch.
2025年7月9日,GMX V1的GLP流動性池受到了巨大打擊。黑客以驚人的4,200萬美元賺了出來。團隊迅速做出了反應,停止了仲裁和雪崩的GLP的交易,鑄造和贖回。損壞包含GMX V1;據報導,GMX V2和GMX令牌是安全的。但仍然...哎呀。
The exploit centered around a design flaw in the GLP token pricing mechanism. Attackers manipulated the calculation of total assets under management, allowing them to mint GLP tokens without proper backing. They then swapped these unbacked tokens for real assets, draining the pool of ETH, USDC, DAI, and more.
利用圍繞GLP令牌定價機構的設計缺陷。攻擊者操縱了管理總資產的計算,使他們可以在不適當備份的情況下鑄造GLP令牌。然後,他們將這些未經背景的代幣交換為真實資產,排除了ETH,USDC,DAI等。
Follow the Money: How the Hackers Moved the Funds
遵循錢:黑客如何搬運資金
Blockchain sleuths have been busy tracking the stolen funds. Initial reports indicate that around $9.6 million was bridged to Ethereum. The hackers used Tornado Cash to obscure their transactions. They swapped USDC for ETH, then converted portions to DAI and other tokens. Classic move, right?
區塊鏈偵探一直在忙於追踪被盜資金。初始報告表明,大約960萬美元與以太坊橋接。黑客用龍捲風現金掩蓋了他們的交易。他們將USDC換成ETH,然後將部分轉換為Dai和其他令牌。經典舉動,對嗎?
GMX responded by offering the hacker a 10% white-hat bounty ($4.2 million!) for the return of the funds. No legal action if they return the rest within 48 hours. Desperate times call for desperate measures.
GMX的回應是,為黑客提供了10%的白帽賞金(420萬美元!)來返還資金。如果他們在48小時內返回其餘的,則無法律行動。絕望的時期要求採取絕望的措施。
DeFi Security Under the Microscope
在顯微鏡下的defi安全性
This exploit raises serious questions about DeFi security. GMX V1 had been audited by Quantstamp and ABDK Consulting. How did they miss this vulnerability? It highlights the limitations of audits, which often overlook protocol-specific risks that attackers later exploit.
這種利用引發了有關Defi安全性的嚴重問題。 GMX V1已由QuantStamp和Abdk Consulting審核。他們如何錯過這個脆弱性?它突出了審核的局限性,審核通常會忽略攻擊者後來利用的特定於協議的風險。
This isn't an isolated incident. Crypto hacks in 2025 have already cost investors billions. Remember the Abracadabra.Finance hack earlier this year? The PancakeSwap v3 launch on Solana looks promising, but security needs to be top of mind.
這不是一個孤立的事件。 2025年的加密貨幣黑客已經使投資者損失了數十億美元。還記得今年早些時候的Abracadabra.Finance Hack嗎? Solana上的Pancakeswap V3發射看起來很有希望,但安全必須是最重要的。
What Can We Learn?
我們能學到什麼?
So, what can we take away from the GMX exploit?
那麼,我們可以從GMX漏洞中奪走什麼?
- Audits Aren't Bulletproof: They're a good start, but not a guarantee of security.
- Protocol-Specific Risks Matter: Generic security reviews often miss the nuances of individual protocols.
- Rapid Response is Crucial: GMX's quick action to halt trading and offer a bounty may help mitigate losses.
My Two Sats
我的兩個坐著
Honestly, this GMX exploit is a bummer. It's a stark reminder that DeFi is still the Wild West. We need better security practices, more thorough audits, and a greater focus on protocol-specific risks. Otherwise, these kinds of incidents will keep happening, and they'll scare away mainstream adoption. The rise of multi-chain solutions like PancakeSwap on Solana also highlight the need for security to be paramount as things become more complex.
老實說,這種GMX漏洞是令人沮喪的。這是一個明顯的提醒,Defi仍然是狂野的西部。我們需要更好的安全慣例,更徹底的審核以及更關注特定於協議的風險。否則,這類事件將不斷發生,它們將嚇到主流採用。索拉納(Solana)上的pancakeswap之類的多鏈解決方案的興起也強調了隨著事物變得更加複雜的安全性,安全性是至關重要的。
Wrapping Up
總結
Despite the bad news, I'm still bullish on DeFi. But we need to learn from these mistakes. Stay safe out there, and always do your own research. Peace!
儘管有壞消息,但我仍然看好Defi。但是我們需要從這些錯誤中學習。保持安全,並始終進行自己的研究。和平!
免責聲明:info@kdj.com
所提供的資訊並非交易建議。 kDJ.com對任何基於本文提供的資訊進行的投資不承擔任何責任。加密貨幣波動性較大,建議您充分研究後謹慎投資!
如果您認為本網站使用的內容侵犯了您的版權,請立即聯絡我們(info@kdj.com),我們將及時刪除。
-

- DNA硬幣,生物技術流媒體和現實世界中的資產:新的邊界?
- 2025-07-10 22:30:13
- 探索DNA硬幣,生物技術流和現實世界資產的融合,重點是Alki David的創新方法。
-

- Transak,炒作令牌和超液體生態系統:深度潛水
- 2025-07-10 23:10:13
- 探索Transak,Hype代幣與超流動生態系統之間的共生關係,研究其生長,整合和未來的潛力。
-

- 瓦斯L2革命:地位網絡的可持續資金模型
- 2025-07-10 23:10:13
- 狀態網絡正在開創一種基於本地收益和應用收入的獨特資金模型的無氣2解決方案。深入了解其開創性方法。
-

- SPX6900和模因硬幣狂熱:騎加密貨
- 2025-07-10 23:30:13
- SPX6900的激增反映了看漲的加密市場,但這是最終的模因硬幣嗎?探索其上升,市場趨勢以及以公用事業為中心的模因硬幣的出現。
-

- FTX債權人,破產索賠:復出故事?
- 2025-07-10 22:50:12
- 從中國債權人爭取其會費的複雜性,到2027年可能的全部回收率。
-

- Bit Mining的Solana Shift:代幣國庫的新時代?
- 2025-07-10 22:50:12
- 礦山挖掘到索拉納(Solana),旨在擁有3億美元的代幣財政部。這是加密礦業多元化的未來嗎?
-

- Solana區塊鏈,Stablecoins和生態系統:乘坐機構採用浪潮
- 2025-07-10 22:55:13
- 通過Stablecoin的整合和遊戲創新來探索Solana在機構融資方面的增長。
-

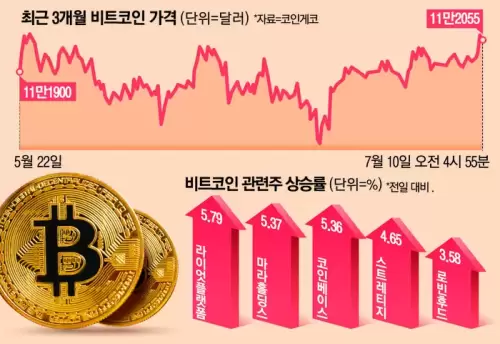
- 比特幣價格飆升:將虛擬資產波乘以新的高點
- 2025-07-10 22:55:13
- 在科技庫存集會和ETF流入的情況下,比特幣達到了新的高點。這是虛擬資產的新常態嗎?
-

- Terra Luna崩潰:風險和恢復中的加密案例研究
- 2025-07-10 23:00:12
- 解開Terra Luna崩潰:經驗教訓,市場影響以及加密貨幣世界中潛在恢復的途徑。