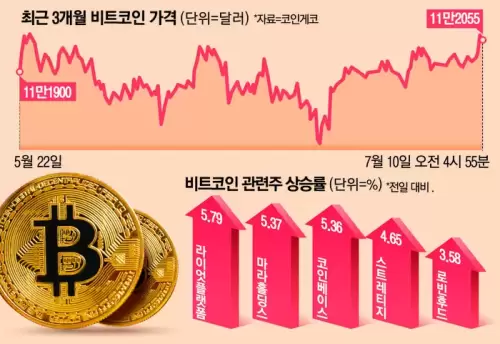
|
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
Cryptocurrency News Articles
GMX Exploit: $42M Liquidity Pool Hack Exposes DeFi Security Flaws
Jul 10, 2025 at 03:54 pm
A deep dive into the GMX exploit, its impact on liquidity pools, and the broader implications for DeFi security. Was it bad luck or a systemic issue?
GMX Exploit: $42M Liquidity Pool Hack Exposes DeFi Security Flaws
Yo, crypto fam! It's been a wild week in DeFi, and not in a good way. The GMX exploit is making headlines, and it's a wake-up call for everyone involved in decentralized finance. Let's break down what happened, why it matters, and what we can learn from it.
What Went Down? The GMX V1 Exploit
On July 9, 2025, GMX V1's GLP liquidity pool on Arbitrum got hit HARD. Hackers made off with a staggering $42 million. The team reacted swiftly, halting trading, minting, and redeeming for GLP on both Arbitrum and Avalanche. The damage was contained to GMX V1; GMX V2 and the GMX token are reportedly safe. But still...ouch.
The exploit centered around a design flaw in the GLP token pricing mechanism. Attackers manipulated the calculation of total assets under management, allowing them to mint GLP tokens without proper backing. They then swapped these unbacked tokens for real assets, draining the pool of ETH, USDC, DAI, and more.
Follow the Money: How the Hackers Moved the Funds
Blockchain sleuths have been busy tracking the stolen funds. Initial reports indicate that around $9.6 million was bridged to Ethereum. The hackers used Tornado Cash to obscure their transactions. They swapped USDC for ETH, then converted portions to DAI and other tokens. Classic move, right?
GMX responded by offering the hacker a 10% white-hat bounty ($4.2 million!) for the return of the funds. No legal action if they return the rest within 48 hours. Desperate times call for desperate measures.
DeFi Security Under the Microscope
This exploit raises serious questions about DeFi security. GMX V1 had been audited by Quantstamp and ABDK Consulting. How did they miss this vulnerability? It highlights the limitations of audits, which often overlook protocol-specific risks that attackers later exploit.
This isn't an isolated incident. Crypto hacks in 2025 have already cost investors billions. Remember the Abracadabra.Finance hack earlier this year? The PancakeSwap v3 launch on Solana looks promising, but security needs to be top of mind.
What Can We Learn?
So, what can we take away from the GMX exploit?
- Audits Aren't Bulletproof: They're a good start, but not a guarantee of security.
- Protocol-Specific Risks Matter: Generic security reviews often miss the nuances of individual protocols.
- Rapid Response is Crucial: GMX's quick action to halt trading and offer a bounty may help mitigate losses.
My Two Sats
Honestly, this GMX exploit is a bummer. It's a stark reminder that DeFi is still the Wild West. We need better security practices, more thorough audits, and a greater focus on protocol-specific risks. Otherwise, these kinds of incidents will keep happening, and they'll scare away mainstream adoption. The rise of multi-chain solutions like PancakeSwap on Solana also highlight the need for security to be paramount as things become more complex.
Wrapping Up
Despite the bad news, I'm still bullish on DeFi. But we need to learn from these mistakes. Stay safe out there, and always do your own research. Peace!
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.





















![Bitcoin is about to plummet and get 9-7W long-term short orders [Chainblade’s latest market BTC technical analysis] July 10, 2025 Bitcoin is about to plummet and get 9-7W long-term short orders [Chainblade’s latest market BTC technical analysis] July 10, 2025](/uploads/2025/07/10/cryptocurrencies-news/videos/bitcoin-plummet-w-term-short-chainblade-market-btc-technical-analysis-july/686f8f4c58e52_image_120_90.webp)